1. Introduction
In this tutorial, we’re going to explain what the attack surface is, what kinds of attack surfaces exist, and also give an explanation of how to use an attack surface management (ASM).
2. What Is an Attack Surface?
Let’s start with a real example. If someone starts working at a technology company, the IT department will most probably give that person a computer with the least privileges they can. Because such policies are built to reduce the risk as much as possible. By defining the attack surface, we can understand how to reduce the risk. In a nutshell, it’s all about reducing the risk, though.
An attack surface refers to the sum of the different parts in which an unauthorized person can try to enter data or extract data from that environment. Within the software domain, it includes all the features, functions, hardware, software, and network interfaces. An attacker can potentially exploit to cause harm or extract data from these environments. Reducing the attack surface is a fundamental technique in improving system security. Therefore, as we said most of the IT departments reduce the risk by limiting the attack surfaces.
3. Attack Surfaces
Security professionals categorize the attack surfaces into three distinct sub-surfaces: The digital, physical, and social engineering attack surfaces. When we consider the whole software domain, it’s feasible to have such categories.
3.1. Digital Attack Surface
As we can understand from the title, the digital attack surface refers to all the digital points of vulnerability where an attacker can attempt to gain unauthorized access to a system or data. It includes vulnerabilities in software, hardware, and network interfaces.
For example, databases, apps, and operating systems can have some vulnerabilities. Because of the “digital” keyword, we may think it’s just related to the software, but physical devices and their interfaces may have hardware vulnerabilities. The network is another crucial topic in ASM. For instance, open ports, associated services, and their weaknesses can have network vulnerabilities. The image below shows the port scanning attack:
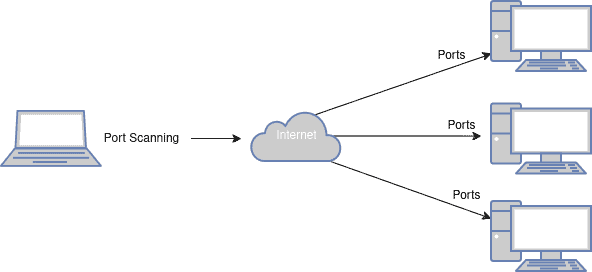
The digital attack surface can expand with the use of cloud services, mobile devices, IoT devices, and other digital technologies. The goal of security practices is to minimize the digital attack surface to reduce the potential for unauthorized access or data breaches.
3.2. Physical Attack Surface
The second category is the physical attack surface. It refers to the physical points where an attacker can attempt to gain access to a system or data. It includes physical access to systems or hardware, such as servers, workstations, and portable devices. Unauthorized physical access can lead to data theft, damage, or unauthorized system control. Physical interfaces like USB ports, CD drives, and physical switches are also part of the physical attack surface.
Again, the main goal of security practices is to minimize the physical surface by securing physical access and interfaces. We can see the USB drop example attack in the image below:
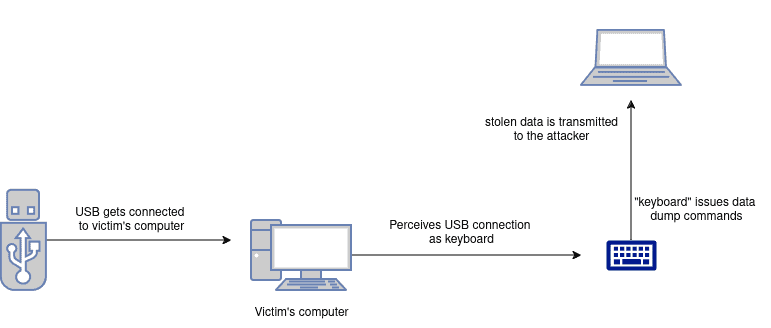
3.3. Social Engineering Attack Surface
Last but not least, the social engineering attack surface covers human points. Attackers can attempt to manipulate individuals into revealing confidential information and perform actions that compromise security. This attack surface involves manipulation techniques and, therefore, tricks individuals into breaking normal security procedures. Phishing, pretexting, baiting, and tailgating are some common methods.
Phishing is one of the most common tactics to trick people and it even becomes the subject of various memes on social media and it happens like in the below image. It usually happens via emails that appear to be from reputable sources. This method aims to deceive individuals into revealing sensitive information. Social engineering attacks can lead to unauthorized access, data breaches, and financial loss. Through user education, awareness, and robust security policies, IT departments aim to minimize the surface of social engineering attacks:
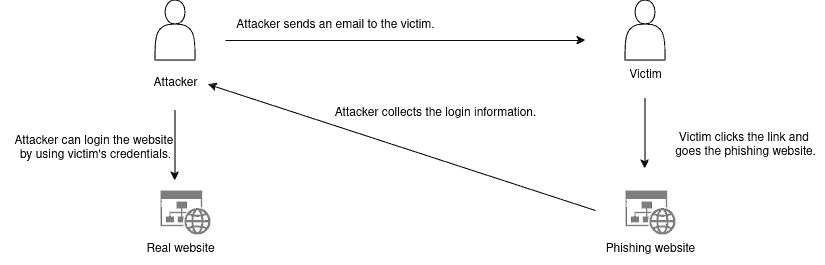
4. What Is an ASM and How to Use It?
Until this point, we’ve defined different categories of attack surfaces and mentioned that the main aim is to reduce the surfaces as much as possible. This is exactly where ASM comes into the stage and creates different principles, strategies, and methodologies to deal with vulnerabilities systematically.
Therefore, it involves the use of strategies and tools. While considering them, it looks from the attacker’s perspective to identify and continuously monitor the organization’s potential vulnerabilities. We can look at some of them separately to understand the overall picture better:
4.1. Continuous Discovery and Monitoring
First, we need to identify the parts that can cause any vulnerability in order to derive some measures. This can start with maintaining an up-to-date inventory of all IT assets exposed to the Internet. It includes those on-premises and in the cloud. The focus is on identifying known assets and overlooked and forgotten IT applications or devices. Once identified, these assets are constantly monitored for any changes.
4.2. Attack Surface Analysis and Risk Prioritization
After detecting such vulnerabilities or attack surfaces, ASM tools evaluate assets based on their vulnerabilities and security risks. After that, it prioritizes them for threat response. This principle is important because prioritization affects the other steps while handling vulnerabilities.
4.3. Attack Surface Reduction
This step is where the exciting part of the IT side starts and where the users can suffer from limited interactions on their devices. Based on their analysis, IT teams can take immediate actions to minimize the attack surface. This can involve enforcing stronger passwords, disabling unused applications and devices, and applying patches. Also, training users to identify phishing attempts, implementing biometric access controls, or updating security policies are part of reducing the attack surface.
4.5. Zero Trust Approach
Finally, the other strategy to reduce the attack surface is the zero-trust approach. It requires all users, even those already within the network, to be authenticated, and authorized. The principles of zero trust are continuous validation, least-privileged access, continuous monitoring, and network micro-segmentation. These principles can help eliminate many attack vectors and provide valuable data for ongoing attack surface analysis.
5. Conclusion
In this article, we explained the attack surface and its different categories. To sum up, understanding attack surfaces and implementing effective attack surface management are crucial aspects of maintaining robust cybersecurity.