1. Introduction
In this tutorial, we’ll investigate how private URLs and password-based authentication can provide access control in networked services. First, we’ll briefly review the concepts of access control. So, we’ll particularly explore private URLs and password-based authentication. Finally, we’ll compare these techniques in a systematic summary.
2. Technological Background
Nowadays, several digital services are provided in a networked way, mainly through the internet. These services may include shopping platforms, administrative systems to organize work schedules, and systems tailored for academic article writing, among many others.
The movement of services and systems to the cloud, making them accessible through networks, got prompted due to two principal reasons:
- Internet popularization
- the emergence of as-a-Service offering models
Cloud computing becomes more and more popular as internet access gets popular. Thus, providers took advantage of cloud infrastructure to host and offer services. So, customers buy services, simply accessing and using them through any machine connected to the internet.
However, this scenario also brought challenges. One relevant of them is how to guarantee that only authorized people access the systems and resources provided through the cloud. So, heterogeneous access techniques have been adopted, such as private URLs and password-based authentication.
3. Access Control
In our context, access control concerns digital resources and systems. Thus, we are not considering any category of physical access control techniques, only logical ones.
In short, access control consists of security techniques that manage who can access resources or systems in a digital environment. Controlling access is essential for reducing risks of data being read and modified or a system being operated by unauthorized entities.
There exist multiple access control techniques, divided into different categories. Here, we’ll focus on two particular access control categories:
- Authentication-based methods: the main objective of authentication is to confirm if an entity is who it claims to be. We can use things these entities know, have, or are to check their identity. So, resources are made available according to each entity’s authorizations policies
- Obscurity-based methods: security by obscurity comes from cryptography. In our context, it provides secure access to a system based on the secrecy of the algorithm that creates access resources. Digital security professionals commonly do not consider obscurity-based methods adequately secure for implementing access control techniques
As previously stated, some methods are intrinsically better than others for implementing a system access control. Although this fact, there are access control techniques implemented with the most varied security methods in practice.
In the following sections, we’ll explore two particular access control techniques: private URLs and password-based authentication.
4. Private URLs
A private URL establishes an access control technique based on security by obscurity. This technique considers unpredictable URLs that, when accessed, grant access to a user for a given resource. So, once the user gets the URL, it simply pastes it in a web browser, for example, to access the resource.
In the private URL technique, we assume the accomplishment of two essential requisites:
- Unpredictable URL generation: the logic and parameters used to generate a private URL may not leak. So, we must keep the generation algorithm in secrecy
- Controlled access to the URL: the access control system provides the private URL using a personal communication channel of the destination user. For example, it may use the user’s e-mail or telephone number
By observing the previously cited requisites, we can consider the private URLs technique as a semi-authentication method.
However, besides the mandatory requisites, other characteristics are desirable and can improve the security of private URLs. Some of the most important ones follow:
- Single-access URL: once generated, private URLs should expire after it first access
- Single-use URL: once used, the systems should never generate the same URL again
- Complex URL: brute force algorithms can not compute the private URL in a feasible timeframe
- Minimum disclosure: pages and data protected by private URLs should not disclose information about the users requesting them
Through the previously cited requisites and characteristics, the private URLs technique gets more secure and practically employable in several scenarios. Examples of suitable applications of private URLs are password reset, account confirmation, and delivery of purchased digital data.
The following image depicts a sequence diagram of using private URLs for resetting a password:
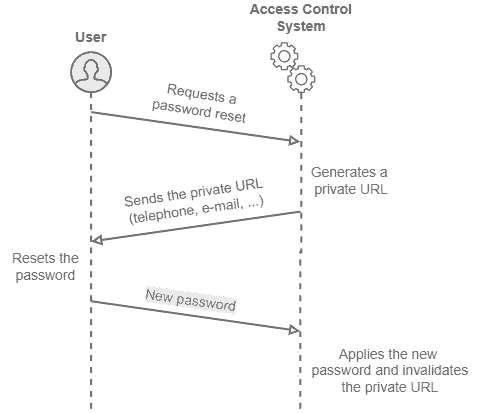
5. Password-based Authentication
Implementing an access control system with password-based authentication means that users must provide personal and secret data to prove their identity. So, the authentication considers things that the user, and only the user, knows.
Passwords, different from private URLs, typically are not a single-access resource. So, we employ the same password multiple times to lead the access control system to authenticate and provide a given data or another type of resource to us.
Given the previously stated characteristics of passwords, we must observe two crucial requisites for creating and maintaining passwords: password generation policy and secure storing of passwords.
Strong passwords are non-trivial and difficult to infer. Thus, password generation policies are adopted to ensure that generated passwords have the proper security level. For example, we can have the mandatory use of non-alphabetic symbols, upper case letters, and numbers while defining a password.
Secure storing, however, enforces that access control systems must store passwords securely, thus avoiding data leakage. Moreover, passwords may never be stored in plain text. In this context, storing schemes typically considers hashing the passwords, saving only a hash code.
Besides the presented requisites, access control systems can adopt renewing password policies. So, the system requests the users to change their passwords after a certain period.
The following image depicts a sequence diagram of a successful authentication in a password-based access control system:
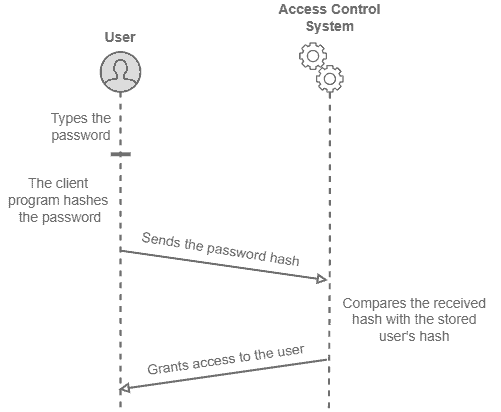
Finally, more sophisticated authentication-based access control systems may use several passwords to authenticate a user at different levels. We call this strategy of multi-step authentication.
6. Systematic Summary
Providing services through the World Wide Web by taking advantage of the cloud architecture (as-a-Service models) became very usual given the recent popularization of internet access.
Once services with market value got moved to the internet, controlling the access to their platforms and resources now represents a vital challenge.
In this context, private URLs and password-based authentication are techniques that play a relevant role in access control systems implementation.
Taking into account the different characteristics and requisites, we can explore the previously cited techniques to deliver adequate resources to the proper users.
The following table compiles private URLs and password-based authentication characteristics and requisites, comparing both access control techniques:
7. Conclusion
In this tutorial, we studied particular access control techniques in computing: private URLs and password-based authentication. First, we reviewed general concepts about access control. So, we explored concepts, requisites, and other characteristics regarding private URLs and password-based authentication. Finally, we compared both explored access control techniques in a systematic summary.
With the provisioning of services through the internet, we can conclude that access control systems play a critical role in the current digital world. These systems enable networked services to provide resources only to specific and authorized users, thus improving services’ security and reliability.