1. Overview
In this tutorial, we’ll look at the buffer overflow attack, and how it works. We’ll also mention different types of buffer overflow attacks. When we talk about security attacks, it’s impossible not to mention countermeasures to mitigate the attacks.
Attackers can use buffer overflow attacks to manipulate the software. Although being a well-known security vulnerability, buffer overflow attacks continue to remain a problem for cyber security teams. Due to the buffer overflow bug in SSL, the threat known as “heartbleed” exposed hundreds of millions in 2014.
2. What Is a Buffer?
In computer science, a buffer, also known as a data buffer or memory buffer, is a region of memory to store data temporarily while it is being transported from one location to another. These buffers are usually stored in RAM. Buffers are often used in computers to increase speed. Most recent hard drives employ buffering to efficiently retrieve data and many online services do as well.
For example, buffers are widely employed to prevent interruptions in internet video streaming. When a video is streamed, the video player downloads and saves around 20% of the video at a time in a buffer before streaming from that buffer. Minor decreases in connection speed or service outrages will not influence video stream performance in this manner.
Buffers are intended to hold a certain amount of data. Except if the software that uses buffer includes built-in instructions to discard data when it receives too much, the application will overwrite data in memory next to the buffer. And here is where the buffer overflow and attack types come into the stage.
3. Buffer Overflow Example
A buffer overflow, also known as buffer overrun, is an information security phenomenon in which a program overwrites nearby memory locations.
Data is temporarily stored in buffers which are storage units in memory. While transferring data from one memory location to another, buffers hold the data. When the amount of data surpasses the memory storage capacity, a buffer overflow occurs. Malformed inputs usually trigger buffer overflows.
When one expects that all inputs will be lower than a particular size and the buffer is constructed to be that size, a malformed transaction that produces more data might force it to write past the end of the buffer. This might cause irregular program behavior, including memory access issues, inaccurate results, and even crashes, if it overwrites nearby data or executable code:
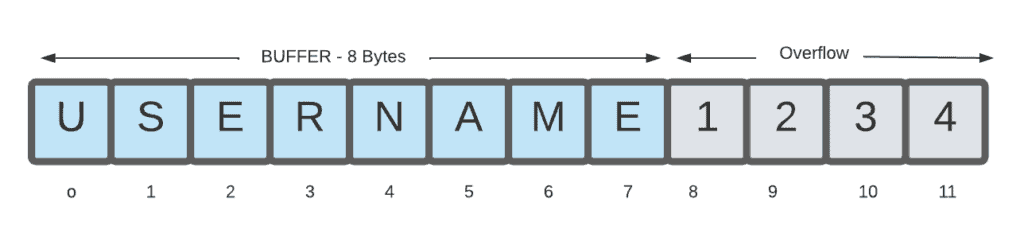
For example, a buffer for log-in credentials can expect a username input of 8 bytes. If a transaction contains 12 bytes which is 4 bytes more than expected, the program can write these 4 bytes over the buffer border. Since the memory over the buffer is not controlled and might be executed as an instruction, attackers can exploit this portion to modify computer memory and then can control the computer.
4. Types of the Buffer Overflow Attack
Programs have different memory regions, and attacks can be categorized by which partition is involved. Stack overflow and heap overflow attacks are the two main types of buffer overflow attacks. There are a number of different other types. Below are the well-known types of buffer overflow attacks:
Stack-based overflow attacks: More often occurring stack-based overflow attacks make use of stack memory, which is only available while a local function is being executed.
Heap-based overflow attacks: On the other hand, heap-based attacks are hard to exploit. They entail flooding the memory space allocated for a program beyond memory used for current run-time activities.
Integer overflow attacks: Arithmetic operations that produce integers that are larger than the integer type intended to keep them are known as integer overflows. This can lead to a buffer overflow attack.
Unicode overflow attacks: By putting Unicode characters into an input that expects ASCII characters, a Unicode overflow can cause a buffer overflow. In ASCII, the letter ‘b’ is represented by the number 98. While ASCII codes only cover Western language characters, Unicode can produce characters for practically every written language on the planet. Because Unicode has so many more characters, many are bigger than the biggest ASCUU character.
5. Countermeasures
Developers usually guard against buffer overflow attacks with two alternative methods. The first of them is incorporating security features in their code. The second of them is employing programming languages that have built-in protection.
While developers can take precautions against buffer overflow attacks, run time protection is also another countermeasure in modern operating systems. OSs usually have three common protections:
- Data execution prevention: OSs can prevent an attack from running code in a non-executable zone by designating certain regions of memory as executable or non-executable.
- Address space randomization: To prevent buffer overflow attacks, OSs also use address space randomization. As we understand from the name, it shuffles the locations of data regions’ address spaces. Buffer overflow attacks usually need the location of the executable code, and it is impossible to perform such attacks when OSs generate address spaces randomly.
6. Conclusion
In this article, we’ve explained what buffer overflow attacks are and how they work. Also, we’ve given some information on different types of them and how we can mitigate such kinds of attacks at different abstraction levels of computing.